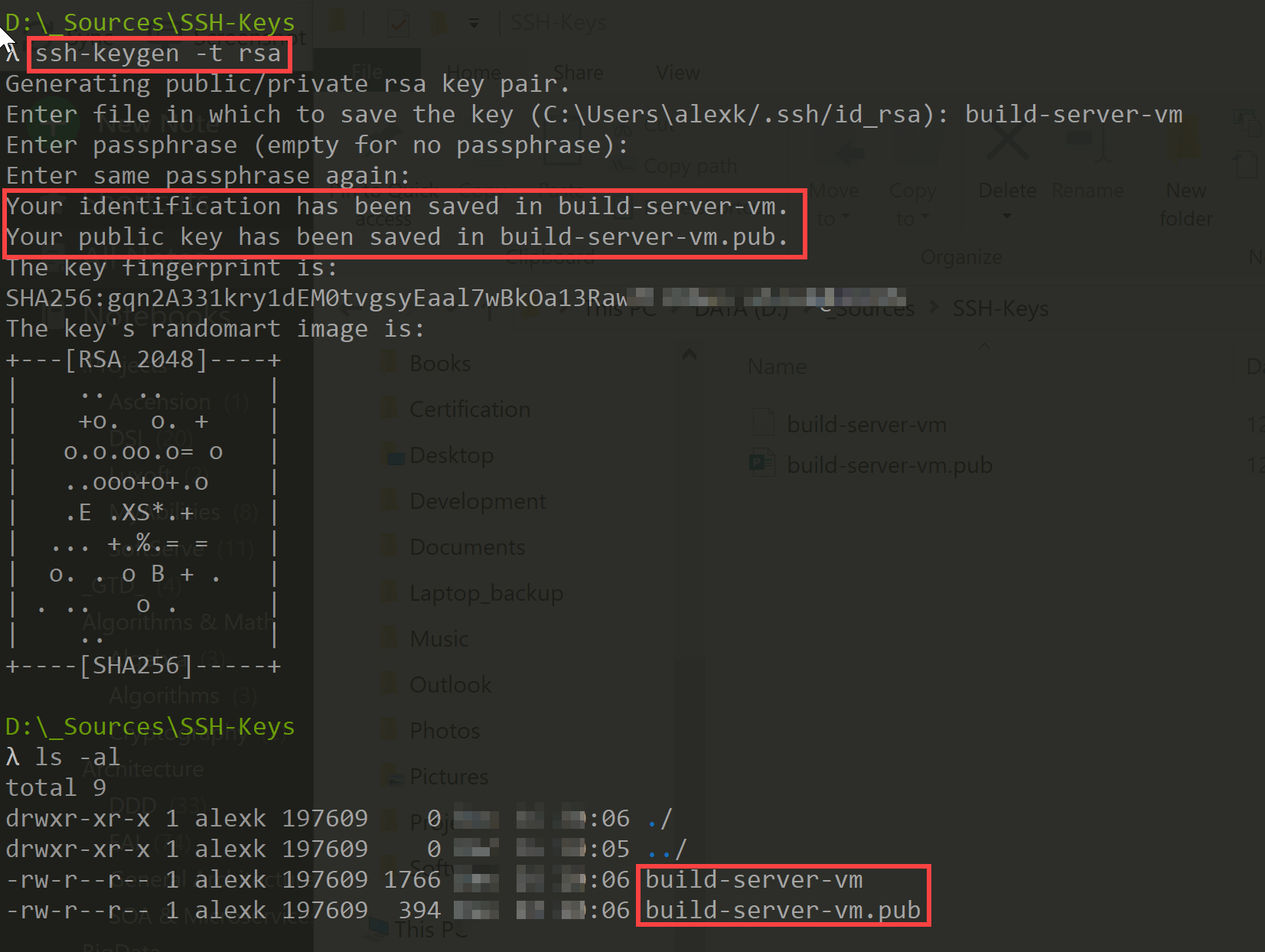
- Generate Ssh Key 4096 Ubuntu
- Gitlab Ssh Key 4096
- Mac Generate Ssh Key 4096
- Ssh Key 4096 Bit
- Generate Ssh Key 4096
To generate a key with OpenSSH, use ssh-keygen: ssh-keygen -t rsa -b 4096 This will generate a 4096 bit RSA keypair and (by default) put it in the (homedir)/.ssh/idrsa location, you can change where it goes at the prompt or specify -f in the command line invocation.
- Ssh-keygen -t rsa -b 4096 ssh-keygen -t dsa ssh-keygen -t ecdsa -b 521 ssh-keygen -t ed25519 Specifying the File Name Normally, the tool prompts for the file in which to store the key.
- Type the following command ssh-keygen -o -b 4096 and press Enter to generate the new key: The -o option was added in 2014; if this command fails for you, simply remove the -o flag.
Why?¶
SSH keys have numerous advantages over passwords
Increased security: they are nearly impossible to brute force or guess
Ease of management: Need access to a friend’s computer? Just send them yourpublic key. No more creating and changing random passwords.
Type less passwords: You can use ssh-agent to cache your key, so you can usessh without typing your password every time
Automated scripts: Because you don’t need to type your password every time,its easier to automate tasks that require ssh
How?¶
Linux/OS X (Short Version)¶
Run this command:
Accept the default location, and enter a secure passphrase that you (and onlyyou) will remember.
Email us the contents of ~/.ssh/id_rsa.pub
Linux/OS X (Detailed)¶
Use the
ssh-keygenutility to create your key. For a 2048 bit RSA key do:
For increased security you can make an even larger key with the -b option. Forexample, for 4096 bits do:
The OSL recommends using RSA over DSA because DSA keys are required to be only1024 bits.
Generate Ssh Key 4096 Ubuntu
When prompted, you can press Enter to use the default location(
/home/your_username/.ssh/id_rsaon Linux, or/Users/your_username/.ssh/id_rsaon Mac) if you don’t already have a keyinstalled, or specify a custom location if you are creating a second key (orjust want to for whatever reason).Enter a passphrase at the prompt. All people connecting to OSL servers mustuse a passphrase. This is just a password used to unlock your key. Ifsomeone else gets a copy of your private key they will be able to log in asyou on any account that uses that key, unless you specify a passphrase. If youspecify a passphrase they would need to know both your private key andyour passphrase to log in as you.
After you re-enter your passphrase, ssh-keygen may print a little picturerepresenting your key ((you don’t need to worry about this now, but it ismeant as an easily recognizeable fingerprint of your key, so you could know ifit is changed without your knowledge - but it doesn’t seem to be widely used))then exit.
Your private key should now be in the location you specified, and your publickey will be at that same location but with ‘.pub’ tacked onto the filename.
Note
If you are creating this key for use with an OSL SSH account, copy and pastethe public key into your ticket. If we didn’t ask you for a public key but youwant one added to your account email it to support@osuosl.org, being sure tospecify who you are and what project(s) you are associated with.

Or, to use the public key on a computer under your control, add it to
~/.ssh/authorized_keys(you can specify multiple public keys, one perline).Never share your private key file, only the public key file.
Windows (using putty)¶
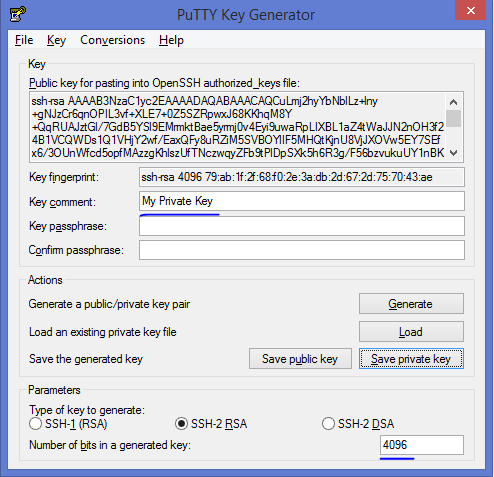
Great guide on setting up Filezilla with ssh keysDownload and start theputtygen.exe generator.
In the “Key” section choose SSH-2 RSA and press Generate.
Move your mouse randomly in the small screen in order to generate the keypairs.
Enter a key comment, which will identify the key (useful when you use severalSSH keys).
Type in the passphrase and confirm it. The passphrase is used to protect yourkey. You will be asked for it when you connect via SSH.
Click “Save private key” to save your private key.
Click “Save public key” to save your public key.
Note
If you are creating this key for use with an OSL SSH account, copy and pastethe public key into your ticket. If we didn’t ask you for a public key but youwant one added to your account email it to support@osuosl.org, being sure tospecify who you are and what project(s) you are associated with.
keep your private key in a safe place
when using putty go to connection->SSH->Auth and Browse to your private key
This is the second post in a series of blog posts on SSH. You can find the series index here. In the last blog post, we had overview of SSH protocol and how SSH authentication works. Then we discussed how to generate an SSH Key pair. As we discussed previously, we need to copy the SSH public key to the remote server and few other connection options. In this blog post, we are going to discuss the same.
Copying SSH Keys to the remote server
There are many ways to copy the public key generated to the remote machine. Below are some of the ways to copy the key.
Copy using ssh-copy-id utility
ssh-copy-id utility is included by default in many linux distributions. This utility makes it very simple to copy your ssh keys to the remote servers. You can easily do this by running below command:
We can specify the file containing public key using the -i option. If this is not specified, it will look for the default file, ~/.ssh/id_rsa.pub. Once you run above command, it will ask you for the password associated with the current account. After typing in the password, the contents of your public key will be appended to the end of the user account’s ~/.ssh/authorized_keys file:
Once its done, you can login into remote machine using command:
Copy without using ssh-copy-id utility
If you do not have the ssh-copy-id utility available, but still have password-based SSH access to the remote server, you can copy the contents of your public key in a different way. For this, first you need to output the contents of the public key and pipe it into the ssh command. On the remote side, you can ensure that the ~/.ssh directory exists, and then append the piped contents into the ~/.ssh/authorized_keys file:
Gitlab Ssh Key 4096
Rest of the process is similar. You will be asked to supply the password for the remote account. After entering the password, your key will be copied, allowing you to log in without a password.
Copying SSH key manually
If you do not have the access to the remote server at all, you can ask the team responsible for performing system administration related tasks on the server. Once they agree to do this for you, you need to find a way to share public key so that they can copy the key on your behalf. Alternatively, the system admins, once they create the user account for you to login to the server, can perform the steps from their side and share private key with you secretly.
Displaying the SSH Key Fingerprint
Each SSH key pair share a single cryptographic fingerprint which can be used to uniquely identify the keys. This can be useful in a variety of situations.
Mac Generate Ssh Key 4096

To find out the fingerprint of an SSH key, type:
Verify the correct location of the public key file. You will be given a string which contains the bit-length of the key, the fingerprint, and account and host it was created for, and the algorithm used:
Connecting to Remote Server using SSH
As we have mentioned previously, that to ssh, you can use the ssh command. In its simplest form, all you need is the IP address of fully qualified domain name of the remote machine:
In this case, it assumes that the username on the server is the same as the current user on the local machine and will try to authenticate against it. However, it may happen that the username on the remote machine is not the same as the current user on the local machine. In such a scenario, you can connect using command:
Most of the SSH servers runs on the default port 22. However if the SSH server is running on a different port, you can specify the same using -p option:
Ssh Key 4096 Bit
Your first time connecting to a new host, you will see a message that looks like this:
If you are using password authentication, you will be prompted for the password for the remote account. If you are using SSH keys, you will be prompted for your private key’s passphrase if one is set, otherwise you will be logged in automatically.
At this point, the system administrators may have configured server to perform some additional actions, such as forcing user to change password for very first login, displaying warning/information in the form of banner, etc.
Running a Single Command on a Remote Server
To run a single command on a remote server instead of spawning a shell session, you can add the command after the connection information, like this:
This will connect to the remote host, authenticate with your credentials, and execute the command you specified. The connection will immediately close afterwards.
Adding the Key to SSH Agent
ssh-agent is a program that can hold a user’s private key, so that the private key passphrase only needs to be supplied once. It will be available for the duration of your terminal session, allowing you to connect in the future without re-entering the passphrase.
Using this utility, a connection to the agent can also be forwarded when logging into a server, allowing SSH commands on the server to use the agent running on the user’s desktop.
Generate Ssh Key 4096
To start the SSH Agent, type the following command into your terminal in the local machine:
This will start the agent program and place it into the background. Now, we can add private keys to it using ssh-add command:
Afterwards, your identity file is added to the agent, allowing you to use your key to sign in without having to re-enter the passphrase again. When run without arguments, it adds the files ~/.ssh/id_rsa, ~/.ssh/id_dsa,
~/.ssh/id_ecdsa, and ~/.ssh/id_ed25519. After loading a private key, ssh-add will try to load corresponding certificate information from the filename obtained by appending -cert.pub to the name of the private key file. Alternative file names can be given on the command line.
Forwarding your SSH credentials
SSH agent can also be used to forward ssh credentials/keys on your behalf to the remote machine. This can be useful in the situations, where you need to connect to another remote server, from the current remote server you are already connected to. It will allow you to authenticate to another server through the server you are connected to, using the credentials on your local computer.
To start, you must have your SSH agent started and your SSH key added to the agent. After this is done, you need to connect to your first remote server using the -A option. This forwards your credentials to the server for this session:
From here, you can SSH in to any other host that your SSH key is authorized to access. You will connect as if your private SSH key were located on this server.
Kill SSH Agent
You can kill ssh-agent using the below command:
It will identify current agent PID running and then proceed to kill the same.
This covers our basics of establishing SSH connection. In next few blog posts, we’ll discuss few options to customize SSH server using various configuration options and SSH clients configuration options as well.
